 In crypto, the wallet is no longer just a tool—it’s an interface, a battleground, and a declaration of intent. As digital assets expand from speculation into decentralized finance, identity, and governance, wallets have matured from simple key managers into programmable, sovereign agents.
In crypto, the wallet is no longer just a tool—it’s an interface, a battleground, and a declaration of intent. As digital assets expand from speculation into decentralized finance, identity, and governance, wallets have matured from simple key managers into programmable, sovereign agents.
This article maps the evolving landscape of crypto wallets—from their technical underpinnings and user experience models to the political and regulatory frictions shaping their future.
Wallet Types: A Changing Taxonomy

1. Hot Wallets
Connected to the internet, these browser, mobile, and desktop wallets (e.g. MetaMask, Trust Wallet) offer speed and ease-of-use. But with convenience comes vulnerability: phishing, malware, and poor key hygiene remain common threats.
2. Cold Wallets
Offline and air-gapped (e.g. Ledger, Coldcard), cold wallets protect keys by isolating them from online access. Excellent for long-term storage, but less ideal for everyday DeFi.
3. Smart Contract Wallets
Wallets like Safe and Argent live on-chain, adding programmable features like multisig, social recovery, spending controls, and gas abstraction. These are the wallets of choice for DAOs and power users.
4. MPC Wallets
Multi-party computation wallets (e.g. ZenGo, Fireblocks) divide private key control among multiple parties or devices. No seed phrase needed—ideal for institutions or users who prefer a recovery model without single points of failure.
5. Custodial Wallets
Platforms like Coinbase or Binance control keys on your behalf. While easy and insured, they contradict crypto’s core principle: “not your keys, not your coins.”
6. Embedded Wallets
Invisible by design, wallets like Magic or Web3Auth use social logins, biometrics, or passkeys to abstract away key management. They power smooth onboarding—but often depend on centralized ID and cloud infrastructure.
Core Technologies & Trends
Keys, Recovery & Security
-
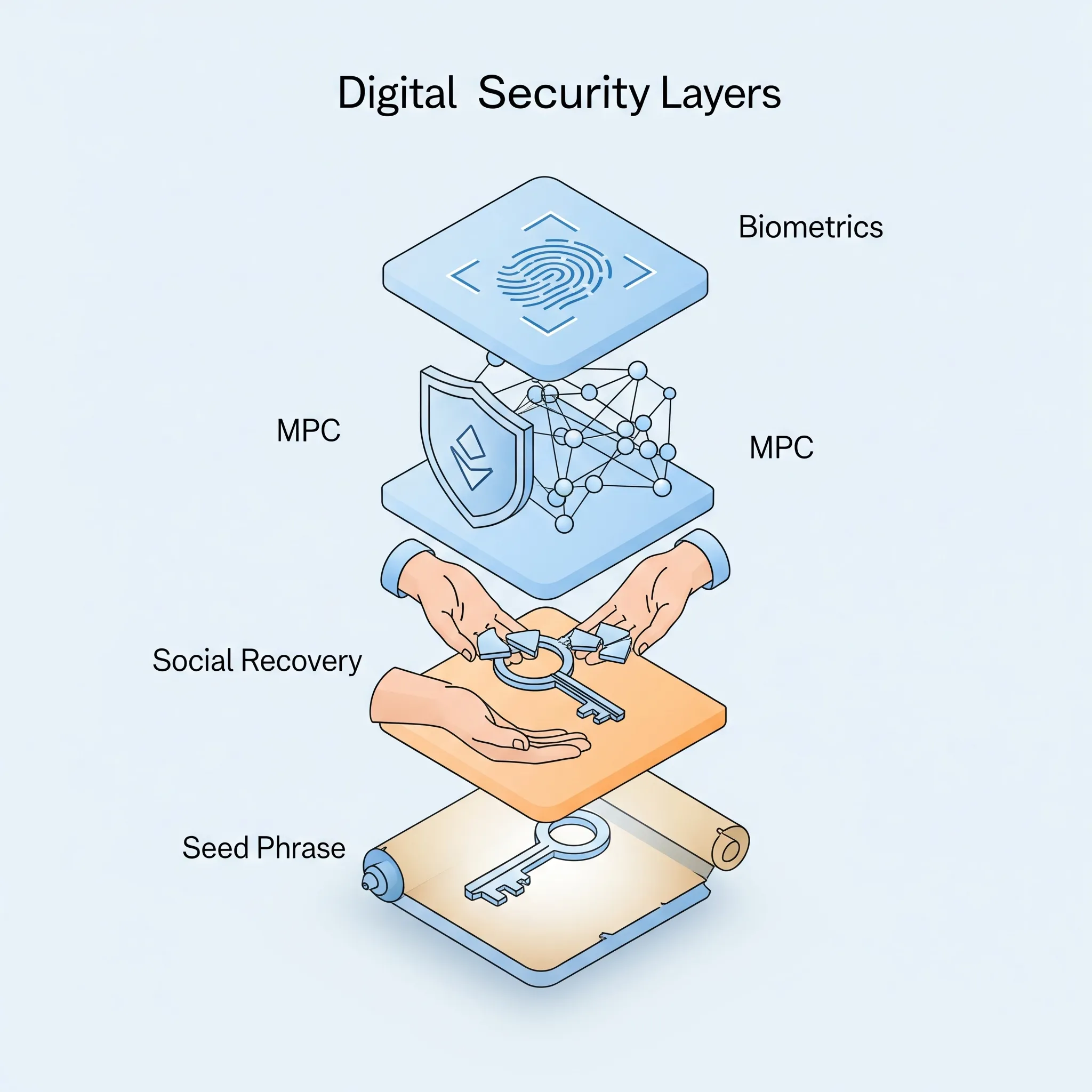
Seed Phrases (12–24 words) remain standard, but face UX and security limitations.
-
Alternatives like MPC, device-bound keys (Secure Enclave), and cloud-encrypted backups are gaining ground.
-
Recovery Innovations include social recovery (Argent), Shamir secret sharing, and custodial shards.
Smart Wallet Features
-
Account Abstraction (ERC-4337): Enables wallets to pay gas in any token, batch actions, add plugin modules, and serve as programmable agents.
-
ZK Integration: Tools like zkLogin and ZKPs introduce selective disclosure, privacy-preserving credentials, and Sybil resistance.
Cross-Chain Interoperability
Wallets like Rabby, XDEFI, and Core streamline UX by aggregating multiple ecosystems (EVM, Bitcoin, Cosmos, Solana) into one interface. No more switching wallets per chain.
Legal, Ethical & Political Stakes
The Samourai Wallet Crackdown
 In 2024, U.S. authorities arrested developers of Samourai Wallet—a privacy-preserving Bitcoin wallet. Their crime? Offering CoinJoin mixing and tools for anonymous spending.
In 2024, U.S. authorities arrested developers of Samourai Wallet—a privacy-preserving Bitcoin wallet. Their crime? Offering CoinJoin mixing and tools for anonymous spending.
The case signals a shift: wallets are no longer seen as neutral tools. Features like anonymity, decentralization, or censorship resistance may now be interpreted as “facilitating money laundering.”
Wallets as Political Statements
-
Custodial Wallets are fully surveilled, often required by law to block or freeze users.
-
Self-custody Tools are being scrutinized for offering too much privacy.
-
Reputation Wallets (e.g. Worldcoin, Gitcoin Passport) introduce access-gated systems—raising ethical questions about who gets to participate in financial ecosystems.
Choosing a wallet is no longer just a UX decision—it’s a statement of sovereignty, privacy, and resistance.
Wallet Comparison Table
| Wallet Type | Examples | Custody | Internet | Recovery | Features | Risks |
|---|---|---|---|---|---|---|
| Hot Wallet | MetaMask, Trust | User | Yes | Seed Phrase | dApp access, portable | Phishing, malware |
| Cold Wallet | Ledger, Coldcard | User | No | Manual Backup | High security, offline | Loss, physical theft |
| Smart Wallet | Safe, Argent | User | Yes | Social/Biometric | Multisig, programmable, gasless | Smart contract bugs, infra reliance |
| MPC Wallet | ZenGo, Fireblocks | Shared/MPC | Yes | MPC Shares | Seedless, team-based | Trust in provider, opaque tech |
| Custodial Wallet | Binance, Coinbase | 3rd Party | Yes | Platform-Managed | Fiat ramps, regulated | Censorship, account seizure |
| Embedded Wallet | Magic, Web3Auth | 3rd Party | Yes | OAuth/Biometric | Invisible UX, social login | Vendor lock-in, identity centralization |
| Air-Gapped Wallets | Coldcard, Passport | User | No | Manual/QR | Maximum isolation, Bitcoin-focused | Cumbersome, limited UX |
Choosing the Right Wallet
Step 1: Prioritize Your Values
| You Care About... | Consider... |
|---|---|
| Convenience | Embedded, custodial, mobile wallets |
| Maximum Security | Hardware, air-gapped, multisig wallets |
| Privacy | CoinJoin tools, local-first wallets |
| Multichain Use | Rabby, XDEFI, Core |
| DAO/Automation | Safe, Taho, account abstraction wallets |
| Regulatory Compliance | Coinbase, Binance |
| Censorship Resistance | Coldcard, Samourai, open-source wallets |
| ### Step 2: Use Case–Based Guidance |
| User Type | Best Wallets | Why |
|---|---|---|
| Newcomers | Coinbase Wallet, ZenGo, Trust Wallet | Easy setup, safety nets |
| HODLers | Ledger, Coldcard, Safe Multisig | Long-term storage, recovery options |
| DeFi Users | MetaMask, Frame, Rabby | Broad support, integrations |
| DAO Members | Safe, Taho, multi-signature wallets | Governance-ready, shared control |
| Privacy Advocates | Coldcard, Samourai, Wasabi | On-chain privacy, local control |
| Builders | WalletConnect, Frame, MetaMask Flask | dApp testing, smart accounts |
| Enterprises | Fireblocks, MPC solutions | Compliance, auditing, multi-user flows |
| ### Step 3: Know the Tradeoffs |
| Tradeoff | What It Means |
|---|---|
| Convenience vs. Control | Easy UX may mean less custody or control |
| Privacy vs. Compliance | Regulatory pressure may penalize private wallets |
| Cross-Chain vs. Depth | One wallet fits all may lose chain-specific features |
| Seedless vs. Secure | New recovery methods may increase central dependencies |
| Programmable vs. Simple | Smart wallets offer power but raise cognitive overhead |
| ## Pro Tips |
-
Use different wallets for different purposes: one for daily use, one cold for storage.
-
Store seed phrases offline and redundantly—ideally with fire/water-resistant solutions.
-
Avoid wallets that are not open source or lack export/recovery options.
-
Keep jurisdictional awareness: privacy tech may be illegal or risky in some regions.
-
Consider wallets that evolve with you—from beginner to advanced, over time.
What's Next for Wallets?
The future of wallets is not just about holding assets—it’s about managing identity, privacy, access, and autonomy. Expect to see:
-
Passkey-based wallets (no seeds, biometric recovery)
-
AI-native wallets (agentic, auto-signing, smart interactions)
-
Onchain identity wallets (DID, zkKYC, verifiable credentials)
-
Modular wallets-as-a-service powering onboarding invisibly
In the end, the best wallet is not just the safest or most convenient—it’s the one that reflects your values and your threat model. In a decentralized world, that’s the ultimate form of self-expression.
#Crypto #Money